Two-Step Verification (also known as Two-Factor Authentication) is a way to increase security on everything from your cellphone to your bank account to your website and more. It is most likely something you have probably started to encounter on a fairly regular basis. However, you, like many people, may be hesitant to use it because you are not really sure how it works and why you need it. So let us lift the veil of mystery for you and explain more about this security feature that you should be using everywhere.
As you probably know from the news and various recent events, internet security breaches and identification theft is at an all-time high and it’s not likely to improve anytime soon. The more we, as a society, depend on technology to advance our lives, we also put ourselves and our businesses at risk for being hacked or having our information stolen. However, there is no reason to panic. New technology is coming out every day to help mitigate these dangers and protect you and your vital information. One of these bits of technology is known by several names – Two-Step Verification, Two-Factor Authentication, or Multi-Factor Authentication.
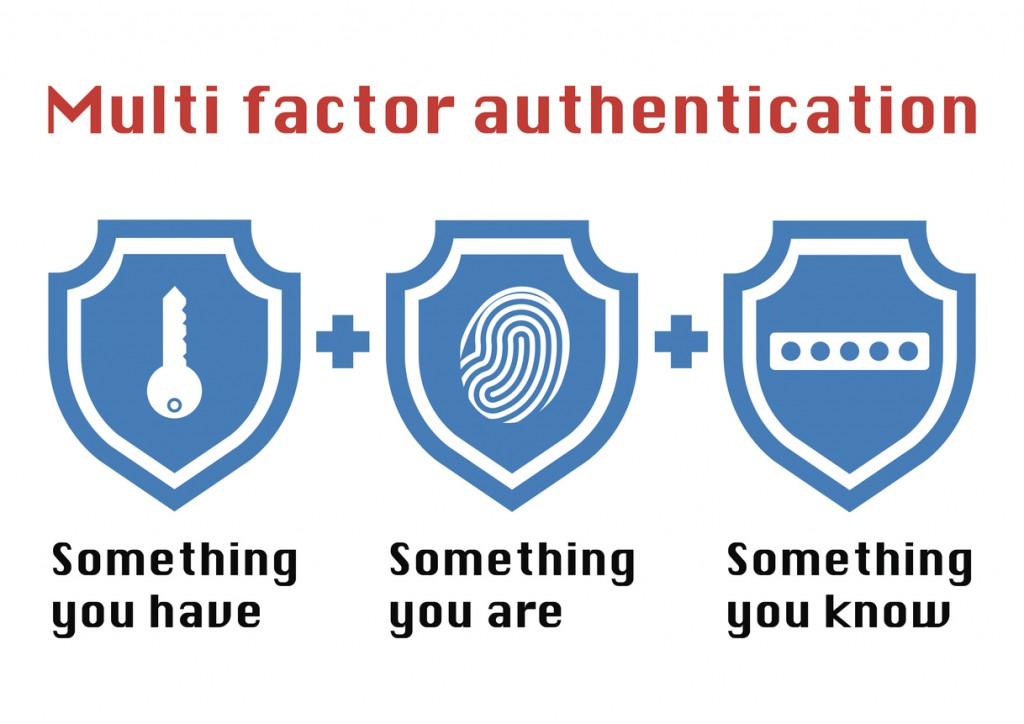
This technology in the IT world is frequently coupled with the phrase “Something you are, something you have, something you know.” What this means is that in order for Two-Step Verification or Multi-factor Authentication to be effective it must have at least two of those things involved to verify or authenticate the identity of the person trying to gain access to the information.
“Something you are” is simply something that is literally you and no one else can have. This is known as inheritance and generally involves some kind of bio-metrics like your fingerprint, a retina scan, voice, typing speed, or a specific pattern that only you do.
“Something you have” is something that you physically have in your possession and is literally known as possession like a bank card, USB stick with token on it, a cellphone, or a key of some sort.
“Something you know” is quite literally something that you know that no one else could know. This is known as knowledge. Examples of something you know is a password, PIN, or answer to a security question.
Some of you might already being using two-factor verification in certain situations and not even be aware of it. Many workplaces require the use of an ID badge that needs to be scanned in order to get through a door only to be followed up by a request for the person to enter a secret PIN. Those are examples of “Something you have” and “Something you know.” That type of multi-level verification process helps to insure that someone who is not authorized to enter is not given access.
But on the internet front more and more websites and businesses are offering the ability to use two-step verification or multi-factor authentication and our advice to you would be, if it is offered, use it! It can only help to protect you.
So how does this work? It’s simple. When you get to a website that offers you two-step verification and you sign up for it – by the way, it’s free to use so another no-brainer – it will ask you several questions about how you want to receive the verification codes. Usually you will get the choices of receiving an email or a text message with a code sent to you on your smartphone. Other sites create a unique set of codes that are assigned only to you that you can download to your computer or print out.
Another method that some banks use is a physical card the size of a credit card that is filled with random numbers only assigned to that card’s registered user. Any time the user tries to do anything that could be a risk to the security of their bank account, the bank requests that the user press the button on the card they possess, “something they have”, and enter the number that appears on the card into the appropriate place on the website. Only if that number matches will they then allow the user to continue with the transaction.
Most sites though offer the security code to your smartphone or email method. This method is fairly secure and really fast as well. Also, the code they send to you expires after a limited amount of time, usually 10 minutes or less. If you haven’t used the code by that time you will have to request a new code.
So basically once you sign up for Two-Step Verification on a website, anytime you try to access that website in the future it will send a one-time verification code to your phone number or email address. Once you receive that code, which usually arrives within seconds, you have to enter that code in the appropriate place on the website in front of you. Once that is done, the website verifies that code is the correct code and lets you into the site to conduct business as usual.
Now some of you might think these added steps are too much of a bother to do and dismiss the idea of Two-Step Verification altogether. However, we want you to really think about how much of a bother it will be if you don’t do it and your valuable information is compromised by the bad guys. Incidents like that happen every day and they damage businesses, personal credit lines, and more. For a few extra seconds of your time, you can go a long way in helping to protect your important personal and business information.
For more information about the pros and cons of Two-Step Verification read this article from the Security Intelligence website!